
- Blockchain Tutorial
- Blockchain - Home
- Blockchain - Introduction
- Blockchain - Double Spending
- Bitcoin - Brief History
- Public Key Cryptography
- Blockchain - Hashing
- Bitcoin - Mining
- Blockchain - Chaining Blocks
- Blockchain - Proof of Work
- Blockchain - Network & Mining
- Blockchain - Incentives to Miners
- Blockchain - Merkle Tree
- Blockchain - Payment Verification
- Blockchain - Resolving Conflicts
- Blockchain - Privacy
- Bitcoin - Mitigating Attacks
- Blockchain - Conclusion
- Blockchain Resources
- Blockchain - Quick Guide
- Blockchain - Useful Resources
- Blockchain - Discussion
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
Blockchain - Proof of Work
As all transactions are time stamped, we need to implement a distributed timestamp server on a peer-to-peer network. This requires some additional implementation and that is the Proof-of-Work that I will describe now. To each block, we now add one more item called Nonce as shown in the figure below −
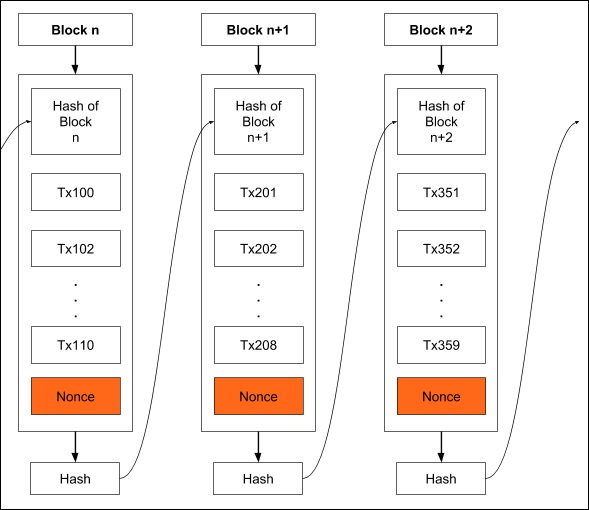
Nonce is a number such that the block’s hash meets a certain criterion. This criterion could be that the generated hash must have its leading four digits to be zero.
Thus, the generated hash would look like 000010101010xxx. Generally, the miner starts with a Nonce value of 0 and keeps on incrementing it until the generated hash meets the specified criterion.
Note that the hash generation works at random and is beyond your control - that is you cannot force the hash function to generate a certain hash. Thus, it may take several iterations until the desired hash with four leading zeros is generated. The expected time for generating a block in bitcoin system is 10 minutes. Once the miner successfully mines the block, he releases that in the system making it now the last block in the chain.
Note that there are multiple miners competing to generate the legitimate block. The Bitcoin system awards the first successful miner by giving him certain bitcoins. In general, the miner with more computing power may be an early winner. This can cause attacks on the entire system by those who possess a huge processing power. I will describe the attacks and how these are mitigated towards the end of this tutorial.