
- Blockchain Tutorial
- Blockchain - Home
- Blockchain - Introduction
- Blockchain - Double Spending
- Bitcoin - Brief History
- Public Key Cryptography
- Blockchain - Hashing
- Bitcoin - Mining
- Blockchain - Chaining Blocks
- Blockchain - Proof of Work
- Blockchain - Network & Mining
- Blockchain - Incentives to Miners
- Blockchain - Merkle Tree
- Blockchain - Payment Verification
- Blockchain - Resolving Conflicts
- Blockchain - Privacy
- Bitcoin - Mitigating Attacks
- Blockchain - Conclusion
- Blockchain Resources
- Blockchain - Quick Guide
- Blockchain - Useful Resources
- Blockchain - Discussion
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
Blockchain - Public Key Cryptography
Public Key Cryptography or in short PKI is also known as asymmetric cryptography. It uses two pairs of keys - public and private. A key is a some long binary number. The public key is distributed worldwide and is truly public as its name suggests. The private key is to be strictly held private and one should never lose it.
In case of Bitcoin, if you ever lose the private key to your Bitcoin wallet, the entire contents of your wallets would be instantly vulnerable to theft and before you know it, all your money (the contents of your wallet) would be gone with no mechanism in the system to trace out who stole it - that is the anonymity in the system that I mentioned earlier.
The PKI accomplies two functions - authentication and the message privacy through encryption/decryption mechanism. I will now explain both these functions −
Authentication
When the two parties exchange messages, it is important to establish a trust between the sender and the receiver. Especially, the receiver must trust the source of message. Going to our earlier scenario (depicted in Figure 1) of Bob sending some money to Lisa for purchasing of some goods from her, let us see how the PKI builds this trust between Bob and Lisa. Look at below image −
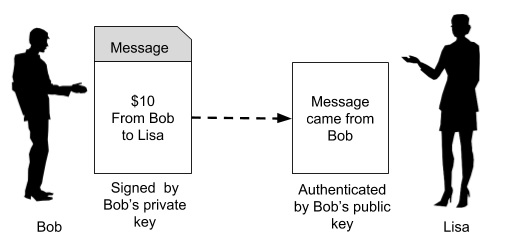
In the first place, if Bob wants to send some money to Lisa, he has to create a private/public key of its own. Note that both keys are always paired together and you can not mix the private and public keys of different individuals or different instances.
Now, Bob says that he is sending $10 to Lisa. So he creates a message (a plain-text message) containing Bob’s (sender) public key, Lisa’s (receiver) public key, and the amount ($10).
The purpose of this remittance such as “I want to buy pumpkin from you” is also added into the message. The entire message is now signed using Bob’s private key. When Lisa receives this message, she will use the signature verification algorithm of PKI and Bob’s public key to ensure that the message indeed originated from Bob. How the PKI works is beyond the scope of this tutorial. The interested reader is referred to this site for a more detailed discussion on PKI. This establishes the authenticity of the message originator. Now, let us look at the message privacy.
Message Privacy
Now, as Lisa has received her payment, she wants to send the link to her ebook which Bob wants to buy. So Lisa would create a message and send it to Bob as shown in image −
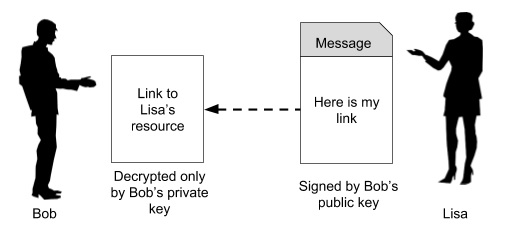
The Lisa creates a message such as “Here is the link to my ebook which you had requested”, signs it with Bob’s public key that she has received in Bob’s request message and also encrypts the message using some secret key which is shared between the two during HTTPS handshake.
Now, Lisa is sure that only Bob can decode the message using the private key that is held by Bob alone. Also, somebody intercepting the message would not be able to recover its contents because the contents are encrypted by a secret key held only by Bob and Alice. This guarantees to Lisa that access to her ebook is granted only to Bob.
Having seen both the features, Authentication and Message Privacy, implied by PKI, let us move ahead to see how Bitcoin makes use of PKI to secure the public ledger that I mentioned in the chapter “What is Bitcoin?”.
For your knowledge − The most popular PKI algorithms are RSA and ECDSA, Bitcoin uses the latter one.